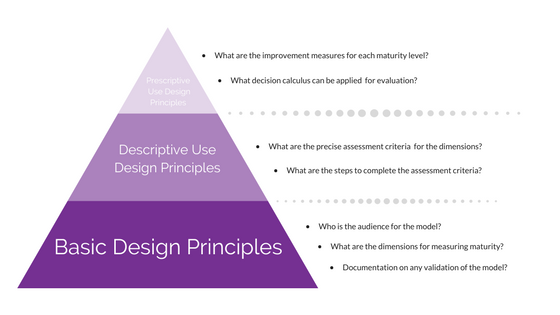
Parallels with the Paradise Papers Investigation
I recently watched the Vice News Tonight hour long show on the Paradise Papers. If you have HBO I highly recommend you give your time to this episode. If you don't have HBO, maybe try one of those free trials and still give it a try and then binge watch Game of Thrones while you are at it. You can also go read more about it on their website, but you won't get the insight into what it took for 400 journalist to hunt through the leaked documents. https://news.vice.com/story/the-paradise-papers-present-a-serious-challenge-for-democracy https://news.vice.com/story/everything-you-need-to-know-about-the-massive-paradise-papers-leak The episode deep dives into the 9 month investigation of the journalists, the different angles they all decided to take on looking at the data, and effort it took to validate their findings. Granted I think about threat hunting close to 12 hours a day, but I couldn't help but see the parallels between the ICIJ journalists methods/...